Hi!
My name is Alec Li and I'm a software engineer at Meta in Menlo Park, having graduated from UC Berkeley with an MS in EECS in 2025, and a BA in Computer Science and Applied Mathematics in 2024.
I also enjoy composing music, playing tetris, swimming, and tackling puzzles I find on the internet!
Research
Alec Li, Samyu Yagati, Raluca Popa
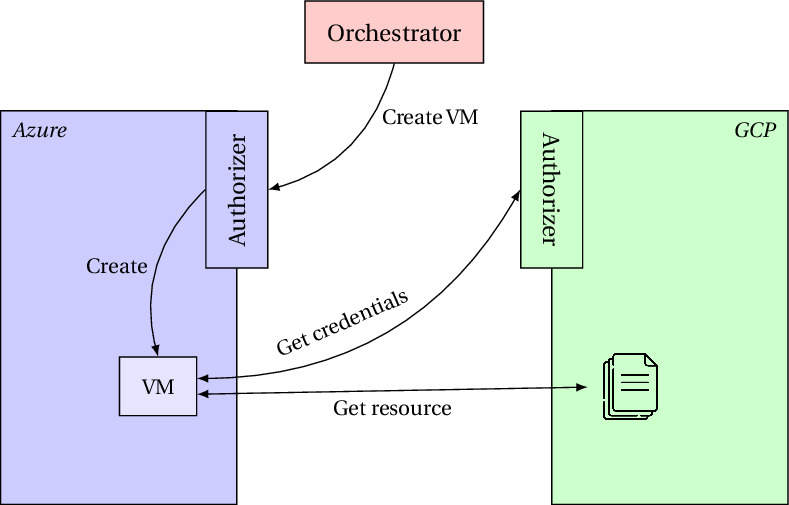
As cloud computing systems evolve over time, there has been an increased dependency on systems that span across multiple cloud providers, leading to the increased usage of workload orchestrator services, to assist with the deployment and management of workloads among multiple clouds. However, the workload orchestrators that exist today all require the end user to disclose their cloud credentials—this means that an adversary that compromises a workload orchestrator can access resources in the user's cloud.
Recently, Skydentity solves one aspect of this security issue, by introducing a system that protects against orchestrator compromise, ensuring that workload orchestrators never hold any cloud credentials, and utilizing proxies that enforce fine-grained user-specified authorization policies. However, VMs created through Skydentity do not have the ability to request resources across clouds, limiting the scope of workloads that can utilize Skydentity.
We introduce an extension of Skydentity that allows for VMs created by workload orchestrators to access resources across clouds, while maintaining the security guarantees of Skydentity, protecting against orchestrator compromise. Our prototype introduces an added latency of at most 3% during VM creation, and has negligible effect on subsequent cross-cloud resource requests.
Samyu Yagati, Alec Li, Karthik Dharmarajan, Romil Bhardwaj, Sam Kumar, Raluca Popa, Malte Schwarzkopf, Ion Stoica

Today’s cloud applications increasingly rely on third-party workload orchestration services that assist with provisioning of cloud resources. Unfortunately, such services require users to hand over their cloud credentials. An attacker who compromises a workload orchestrator can therefore access sensitive data and code in the user’s cloud deployment.
Skydentity solves this problem with request permissions, which decouple the permission to manage resources from the permission to access resources. To do so without cooperation from cloud providers, we implement Skydentity as a proxy that interposes on workload orchestrator requests to cloud providers, checks them against user-provided policies, and provides credentials only to authorized requests. Using a design inspired by capability-oriented authorization, Skydentity restricts the operations a workload orchestrator can perform to those pre-authorized by a user policy, and always prevents the workload orchestrator from accessing user credentials.
Our prototype of Skydentity supports a range of typical workload orchestration use cases, such as job management, data management, and analytics, and imposes modest overheads. Added cost is 1.75 cents or less for a typical workload, and latency overheads are at most 3% for VM-based jobs and 20% for storage jobs on clouds that support scoped tokens.
Projects